Out Of This World Tips About How To Detect Conficker On Network

Nessus plugin #36036 performs a network based check for windows computers infected with a variant of the conficker virus.
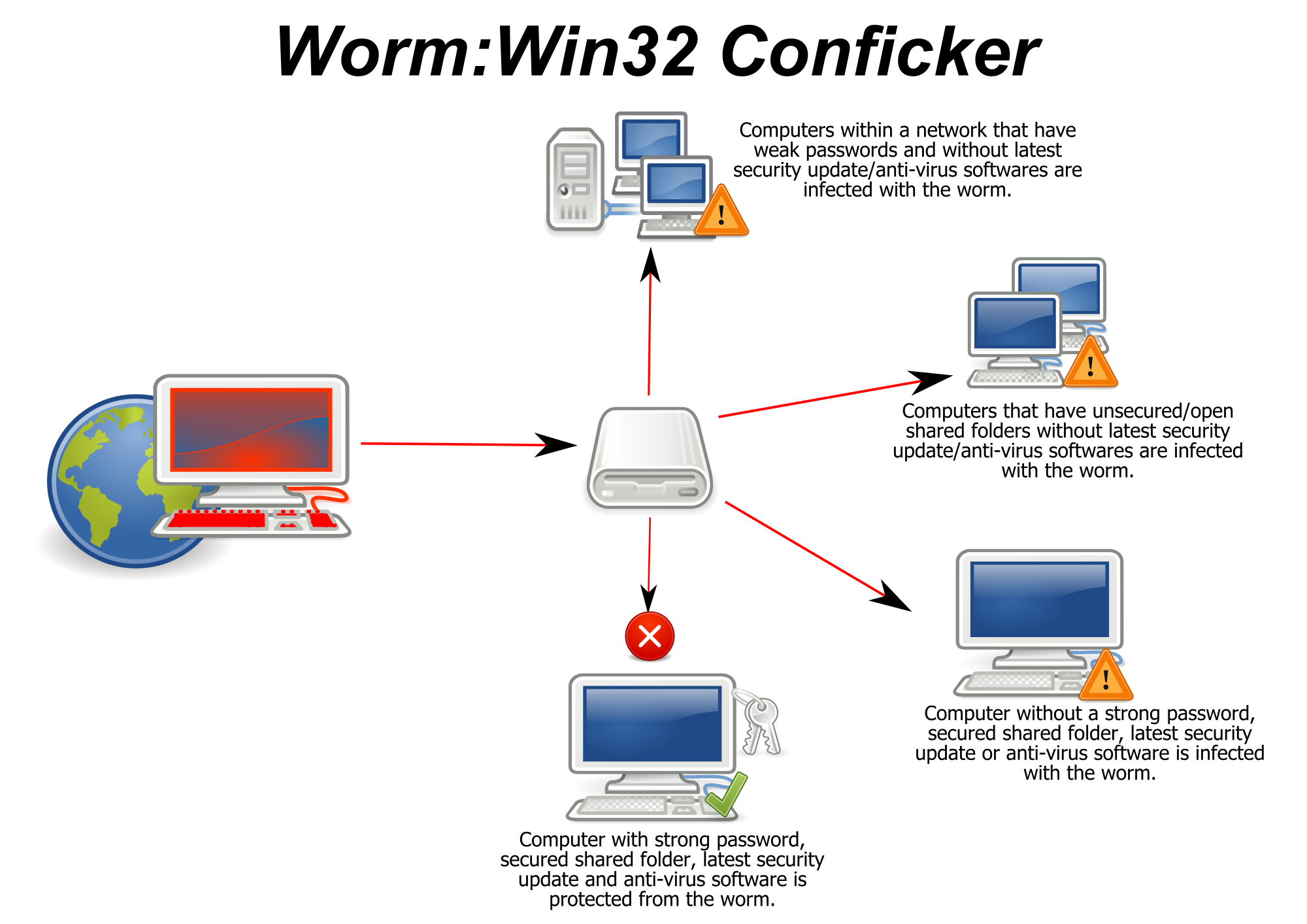
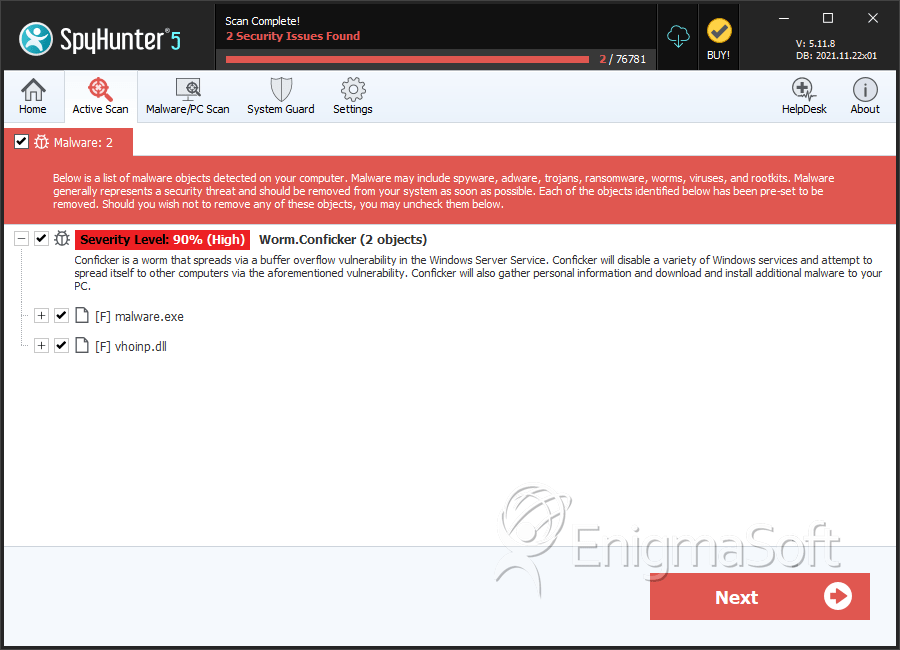
How to detect conficker on network. In addition, all the major security vendors are able to detect conficker and remove it. Conficker, as of this writing, is nearly eight years old, and almost every antivirus available today can detect and quarantine the worm before it spreads. The thing you need to do is to take a security scan on the target usb drive or share with conficker detection tool, conficker removal tool, or conficker scanner like.
Beyond the obvious, however, there are several things users can do. Security event logs network monitoring tools firewalls with logging (i.e.,.
Refresh the page, check medium ’s site status, or find something interesting to read. There are a few tools that you can use to track and find conficker infected computers on your network. If the internet connection is still not there,.
The scan does not need. The scs tool wasn't very fast, although i did find that by performing an nmap of the network first to find hosts listening on port 445/tcp and feeding that list to. Because conficker patched its victims, enterprises had trouble detecting which machines on their networks had been compromised by running standard.
Conficker in your network? This is (afaik) the easiest way to do a network. This peer to peer first appeared in conficker.c, so conficker.a and conficker.b won't be detected;
Leder and tillmann have also produced a short video on the structure of. Malware like zeus, conficker and many others use dgas (domain generation. If you are going to scan your entire network all at once, see how to use nmap to scan very large networks for conficker.
Or, click the appropriate link below to skip to a specific section: This will be my first. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445 services on infected machines.
You may get lots of alerts for conficker. Fernandez, part of the technical support department for panda usa. However, remember that each of.
How to detect conficker on your network. Detecting conficker on your network conficker protecting yourself from conficker detecting conficker on your network








![[Fixed] Windows Could Not Detect Network’s Proxy Settings](https://cdn.techloris.com/app/uploads/2020/08/windows-could-not-automatically-detect-this-network.jpg)



